Step 3e: ZWave - Security
The code for this step is found here.
One final change to our demo. Let's make the sensor and configuration classes secure. We'll use S0 so the zpiffer/zniffer can decrypt the packets, although setting up S2 would be simple.
The first edit is to src/config_app.h. Define REQUESTED_SECURITY_KEYS as SECURITY_KEY_S0_BIT. For S2 you would also OR in SECURITY_KEY_S2_UNAUTHENTICATED_BIT and SECURITY_KEY_S2_AUTHENTICATED_BIT.
The second edit is to our application. We don't need to change any functions, just create two arrays with the secured command class lists and add them to the NIF. The global arrays are named cc_open_secure and cc_secure. Move the COMMAND_CLASS_MULTISENSOR_ and COMMAND_CLASS_CONFIGURATION byte from cc_unsecure to cc_secure, and put COMMAND_CLASS_SECURITY in all three. Replace the NULL, 0 entries in appnif1 with the arrays and their length.
The third edit is to the sensor command class. Security when sending packets is controlled by flags in the transmit options. Our implementation in Step 3c has two triggers for sending a value: an incoming GET, or a button press. For the first the receive options will contain the security flags and the translation in the framework's RxToTxOptions() function will preserve them, so the reply will be encrypted if needed. For the second we faked receive options. Now, sendSensorValue() will check if we have an S0 key and set the appropriate flag, before translating to transmit options and sending.
In the project
-
Link ${SDK}/ZAF/CommandClasses/Security/CC_Security.c under ZAF_CC/.
-
Link on the file system ${SDK}/ZAF/CommandClasses/Security/CC_Security.h under ZAF_CC/.
Our changes are
|
object |
status |
role |
description |
|
appnif1 (global var) |
edit |
transport |
mark secure command classes |
|
REQUEST_SECURITY_KEYS (config_app.h) |
edit |
security |
enable S0 |
|
sendSensorValue (CC_MultiSensor.c) |
edit |
security |
button press sends values securely |
The final project file listing is
|
hw/ |
src/ |
ZAF_AppUtil/ |
ZAF_CC/ |
|
displayconfigapp.h |
config_app.h |
ZAF_TSE.c |
CC_Configuration.c |
|
displayfont16x20HT.h |
config_rf.h |
|
CC_Configuration.h |
|
em_types.h |
HTSensor1.c |
|
CC_MultiSensor.c |
|
graphdisplay.c |
i2cspmconfig.h |
|
CC_MultiSensor.h |
|
graphdisplay.h |
|
|
CC_Version.c |
|
textdisplay.c |
|
|
|
|
testdisplayconfig.h |
|
|
|
|
textdisplay.h |
|
|
|
|
linked within Simplicity Studio |
|||
|
display.c |
|
application_properties.c |
CC_Supervision.c |
|
displayls013b7dh03.c |
|
AppTimer.c |
CC_Security.c |
|
displaypalemlib.c |
|
board_BRD420x.c |
multichannel.c |
|
em_i2c.c |
|
board_indicator.c |
|
|
em_letimer.c |
|
board.c |
|
|
em_prs.c |
|
ZAF_command_class_utils.c |
|
|
gpiointerrupts.c |
|
zaf_event_helper.c |
|
|
i2cspm.c |
|
ZAF_network_learn.c |
|
|
startup_zgm13.S |
|
ZAF_uart_utils.c |
|
|
system_zgm13.c |
|
ZW_TransportEndpoint.c |
|
|
|
|
ZW_TransportMulticast.c |
|
|
|
|
ZW_TransportSecProtocol.c |
|
|
linked on file system |
|||
|
|
|
|
CC_Common.h |
|
|
|
|
CC_Security.h |
|
|
|
|
CC_Supervision.h |
|
|
|
|
CC_Version.h |
|
|
|
|
multichannel.h |
With these changes the sensor readings are now sent secured.
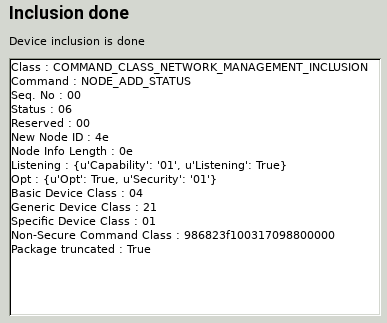
zipgateway information after secured inclusion. Command class list includes both unsecured (0x98 Security, 0x68 ZIP Name, 0x23 ZIP, 0xF1 S0_Mark) and secured (0x31 MultilevelSensor, 0x70 Configuration, 0x98 Security).
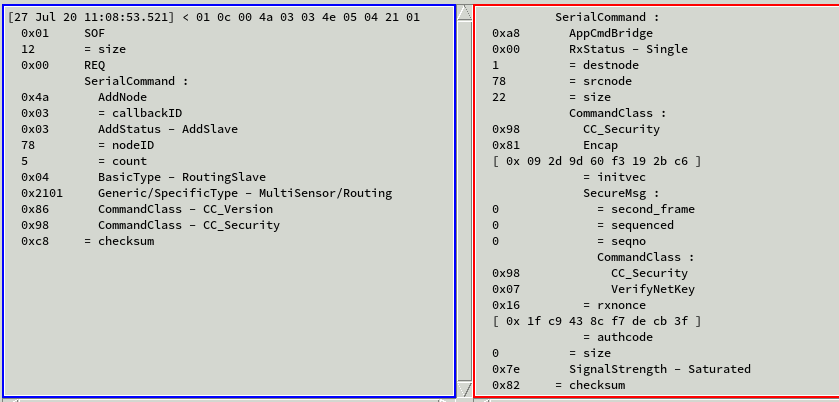
zpiffer trace of inclusion. AppUpdate in left (blue) window shows only unsecured command classes. Right (red) window has network key verification from device to host.
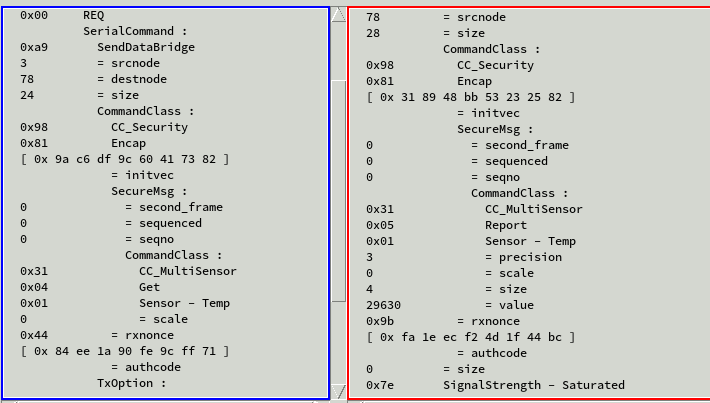
Secured GET (left/blue) and REPORT (right/red) sequence for temperature reading. Nonce frame not shown.
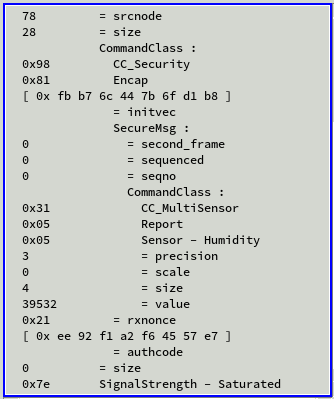
Button press sends secured humidity reading.
We'll wrap up the project with a review of all that's been done and an introduction to the other pieces of the framework.
